Security Researchers Lose a Favorite DNS Recon Tool Jan 2018
Let's Encrypt announced this week they will begin issuing wildcard SSL certificates starting January 2018, a feature many have been hoping would be added to the service for years. While many will be rejoicing, it may get a little harder locating scammers and phishers.
While the vast majority of Let's Encrypt issued certificates are for legitimate domains, the service has become a sort of best practice for phishing campaigns. Why? SSL brings the illusion of trust to a URL. This has been compounded with most browsers indicating a site is secure in the URL bar, by merely serving a site up via HTTPS. Combine this with the fact that Let's Encrypt is a completely free service, and you have a breeding ground for scammers.
One reliable method security researchers use to enumerate domain names (determine all sub-domains of a domain name) is to monitor SSL certificate issuance. The Certificate Transparency project makes this easy.
For example, here is the data pulled from Google's Certificate Transparency system for a domain I manage. The staging and demo sub-domains aren't really for public consumption, and were used previously for testing, but since I used Let's Encrypt to issue SSL certificates for the sub-domains, they sit here plain as day.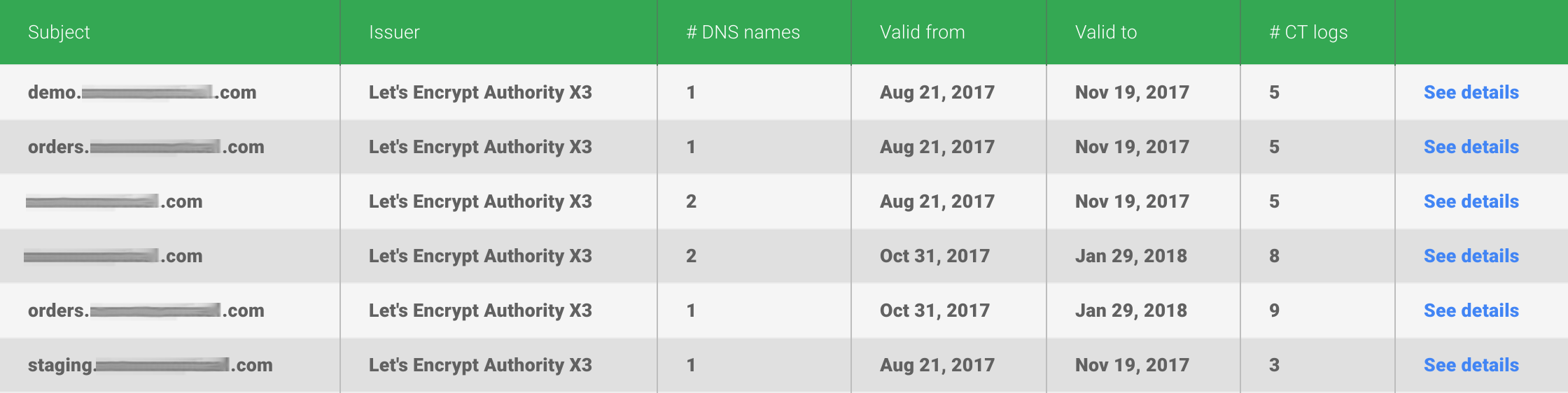
One strategy phishers use to make a URL seem legitimate is to prepend sub-domains to a scam domain. Of course, it's not going to be demo, but instead something like www.paypal or mail.google. Here's a pull of a real phishing domain.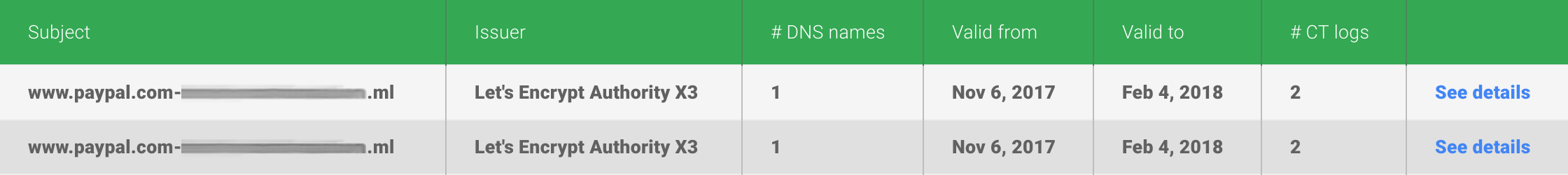
To date, since each distinct domain name protected by Let's Encrypt needed to be added to the SSL certificate separately, and since Let's Encrypt is so widely used by phishers, this type of DNS recon has been an effective way to uncover phishing threats. Scammers can now conceal their campaigns - easily, and for free - by utilizing a wildcard certificate, so the phishing sub-domain does not appear within the Certificate Transparency project.
I'm very supportive of the mission Let's Encrypt has of encrypting the entire web. Every site should be using SSL in this day-and-age to protect user privacy. But, just because a site is served up via SSL it doesn't mean it's secure. A site may be compromised and hosting malware, or you may have arrived on the site via a cleaver XSS vulnerability, or the URL may look legitimate but is in fact part of a clever phishing campaign. It's just going to be a little harder fishing for phishers in a couple months.
Posted: Nov 16, 2017
Keyword tags: infoseccybersecuritycertificate transparencylets encryptphishing
Recent Posts:
Popular Posts:
Recent Security Posts:
S3 Buckets: Now With Both Leak & Fill Vulnerability
Stealing Data With CSS: Attack and Defense
Move Over S3: Open Directory Indexes Continue to be a Problem
Security Researchers Lose a Favorite DNS Recon Tool Jan 2018
KRACK: How To Protect Yourself on a Flawed Network
Equifax, SEC, & Now Deloitte: Organizations Must Employ Offensive Security
